Splunk BOTS: A Defend the Flag Full Mock Exercise
November 26, 2024
I recently had the pleasure of attending the November 15 Splunk Boss of the SOC (BOTS) CTF event hosted by Cybersecurity Ontario and Splunk. The event organizers asked that we not share any details of the CTF scenarios, however I will share my general experience at the event.
The BOTS event is a blue team capture the flag (CTF) event, although I would call it a defend the flag (DTF) event. The event was a full mock exercise with four attacker scenarios and our task was to investigate each scenario. The investigation was simulated through a series of questions. Answers to the questions were scored according to correctness and how quickly we answered. For an idea of the scenarios see the public dataset and instructions on how to acquire the question set for a past BOTS event.
The event was an in-person event and we were arranged into teams of four. We could form our own teams, and since I didn't know anyone else going to the event I formed a team with three other people whom I'd never met before. Since I initiated creating the team via the BOTS website, I dubbed ourselves team HeavyMetal 🤘 hoping this would attract some metalheads. Although this did not work I did end up with a great team and we managed to place 5th out of 18 teams. Not bad since this was the first time any of us had attended a blue team DTF event, although I did practice Splunk leading up to the event and my cybersecurity program teaches a similar tool called Sumologic.

Figure 1: Our team, myself wearing the obligatory Iron Maiden t-shirt, as is tradition
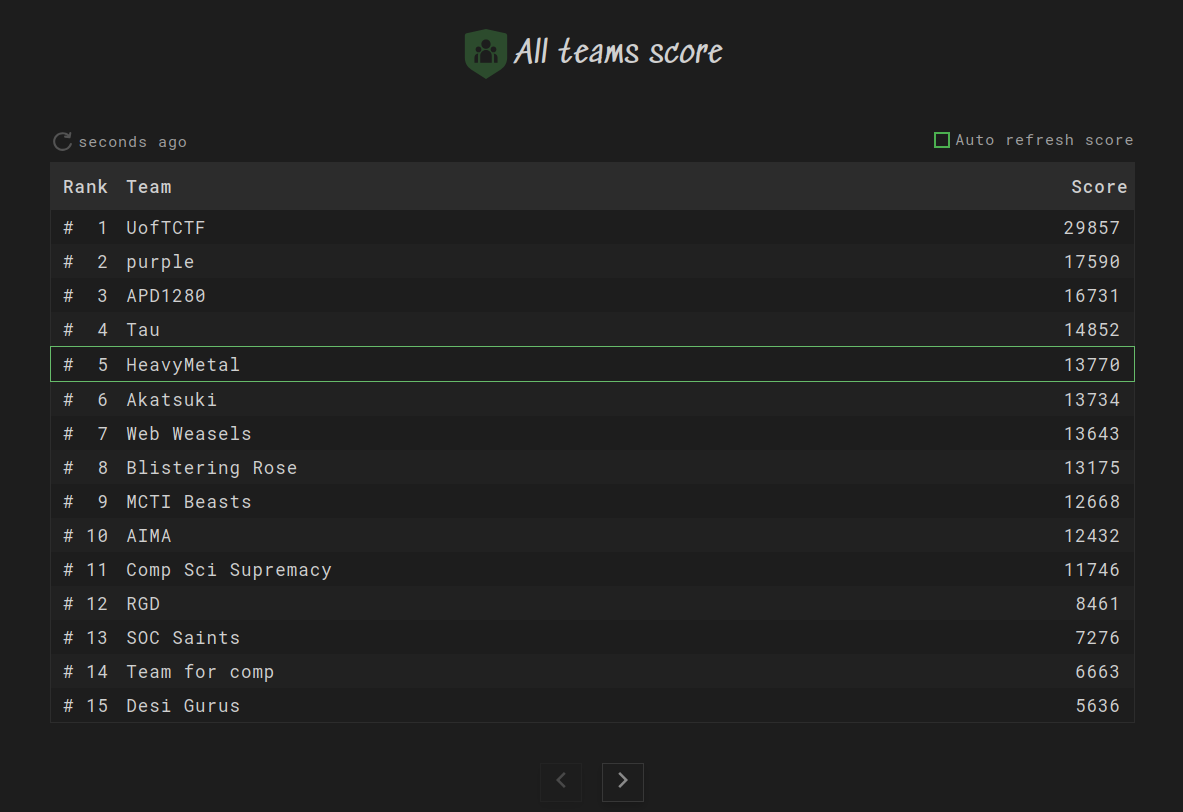
Figure 2: Leaderboard
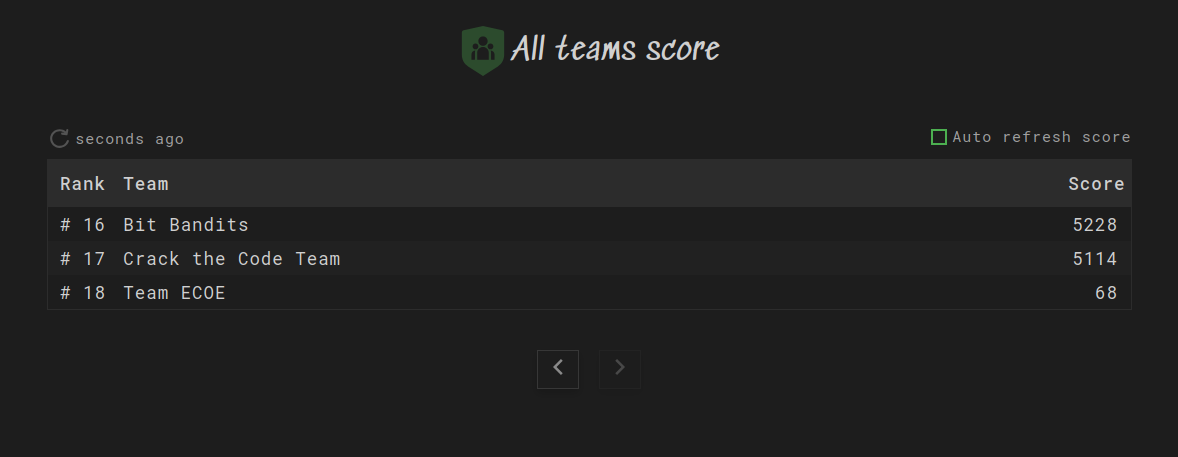
Figure 3: Leaderboard
The event itself was an intense 4 hours of non-stop querying, analyzing, and threat hunting using Splunk. We worked with log data from AWS CloudWatch, AWS CloudTrail, AWS EKS, web servers, Slack, and other sources looking for signs of infiltration, data exfiltration, and other attacker shenanigans. There was also a bonus easter egg 5th scernario which was more light hearted. The event was a whirlwind and I would not say I understood everything we were looking at in the logs. However it was great to get an experience of what it might be like to work in a security operations center (SOC) "for real", or at least as close as possible to for real.